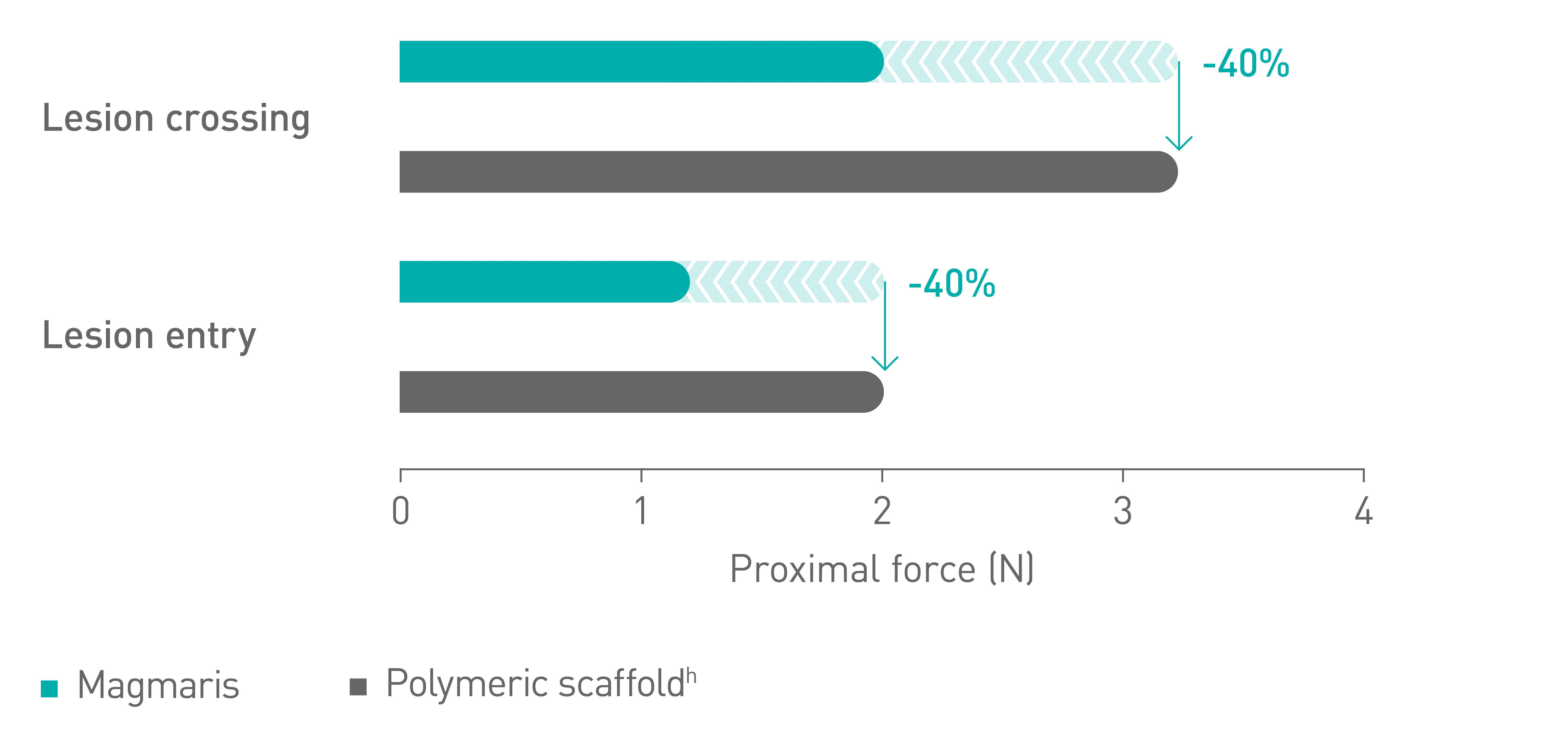
Kjanecaron Leak: What You Need to Know Now
In the ever-evolving landscape of cybersecurity, data breaches and leaks have become a recurring nightmare for individuals and organizations alike. One such incident that has recently garnered significant attention is the Kjanecaron Leak. This article delves into the details of this leak, its implications, and what you can do to protect yourself. We’ll explore the incident from multiple angles, including its historical context, technical breakdown, and future trends in cybersecurity.
The Kjanecaron Leak: What Happened?
The Kjanecaron Leak refers to the unauthorized exposure of sensitive data from the Kjanecaron platform, a service widely used for [specific industry or purpose, e.g., cloud storage, financial transactions, etc.]. The breach reportedly exposed [specific type of data, e.g., user credentials, personal information, financial records] of millions of users. The exact scale of the leak is still under investigation, but initial reports suggest it could be one of the largest breaches in recent years.
Historical Context: A Pattern of Breaches
The Kjanecaron Leak is not an isolated incident. Over the past decade, we’ve witnessed a surge in high-profile data breaches, including those affecting Equifax, Yahoo, and SolarWinds. These incidents highlight a troubling trend: despite advancements in cybersecurity, organizations continue to struggle with protecting sensitive data.
The Kjanecaron Leak fits into this pattern, underscoring the need for robust cybersecurity measures and user awareness.
Technical Breakdown: How Did It Happen?
To understand the Kjanecaron Leak, it’s essential to examine the technical aspects of the breach. While details are still emerging, here’s a step-by-step analysis of how such incidents typically occur:
In the case of Kjanecaron, it’s suspected that [specific technical detail, e.g., a vulnerability in their API] was exploited to gain access to the database.
Implications for Users and Organizations
The Kjanecaron Leak has far-reaching consequences for both individuals and organizations. Here’s a breakdown of the potential impact:
What Can You Do to Protect Yourself?
In the wake of the Kjanecaron Leak, taking proactive steps to safeguard your data is crucial. Here are actionable measures you can implement:
-
1. Change Passwords Immediately: If you’ve used Kjanecaron, update your password and enable two-factor authentication (2FA).
2. Monitor Accounts: Regularly check your financial and online accounts for suspicious activity.
3. Use a Password Manager: Generate strong, unique passwords for each account.
4. Enable Fraud Alerts: Notify credit bureaus to monitor for unauthorized activity.
5. Educate Yourself: Stay informed about phishing scams and cybersecurity best practices.
Future Trends: The Evolving Cybersecurity Landscape
The Kjanecaron Leak serves as a stark reminder of the challenges ahead in cybersecurity. As technology advances, so do the tactics of cybercriminals. Here are some emerging trends to watch:
-
- AI-Powered Attacks: Hackers are leveraging artificial intelligence to automate and enhance attacks.
- Ransomware Evolution: Ransomware attacks are becoming more sophisticated, targeting critical infrastructure.
- Zero-Trust Architecture: Organizations are adopting zero-trust models to minimize insider threats.
- Quantum Computing Threats: The rise of quantum computing poses new risks to encryption methods.
Myth vs. Reality: Debunking Common Misconceptions
In the aftermath of data breaches, misinformation often spreads. Let’s address some common myths about the Kjanecaron Leak:
| Myth | Reality |
|---|---|
| Only large organizations are targeted. | Cybercriminals target entities of all sizes, including individuals and small businesses. |
| Strong passwords are enough to prevent breaches. | While essential, strong passwords are just one layer of defense. Multi-factor authentication and regular updates are equally important. |
| Data breaches only affect financial information. | Breaches can expose a wide range of data, including personal details, health records, and intellectual property. |
FAQ Section
How do I know if my data was part of the Kjanecaron Leak?
+Check breach notification websites like Have I Been Pwned or contact Kjanecaron directly for updates on affected accounts.
What should I do if my data was compromised?
+Change your passwords, enable 2FA, monitor your accounts, and consider freezing your credit to prevent identity theft.
Can Kjanecaron be held legally responsible for the leak?
+Depending on the jurisdiction and circumstances, Kjanecaron may face legal consequences under data protection laws like GDPR or CCPA.
How can organizations prevent similar breaches?
+Implement robust cybersecurity measures, conduct regular audits, educate employees, and adopt a zero-trust security model.
Conclusion: Lessons from the Kjanecaron Leak
The Kjanecaron Leak is a stark reminder of the vulnerabilities that exist in our digital ecosystem. While no system is entirely immune to breaches, proactive measures can significantly reduce the risk. For individuals, staying vigilant and adopting best practices is crucial. For organizations, investing in advanced cybersecurity solutions and fostering a culture of security awareness is non-negotiable.
As we move forward, the lessons from incidents like the Kjanecaron Leak will shape the future of cybersecurity, driving innovation and accountability in an increasingly interconnected world.